Porty is an Android quiz application which has carefully curated multiple-choice quizzes based on topics from PortSwigger’s Web Security Academy series. Empowering you to understand secure coding practices and application security principles. Porty delivers a fun and challenging experience that enables users to test their knowledge on various Application Security topics such as: Target Audience[…]
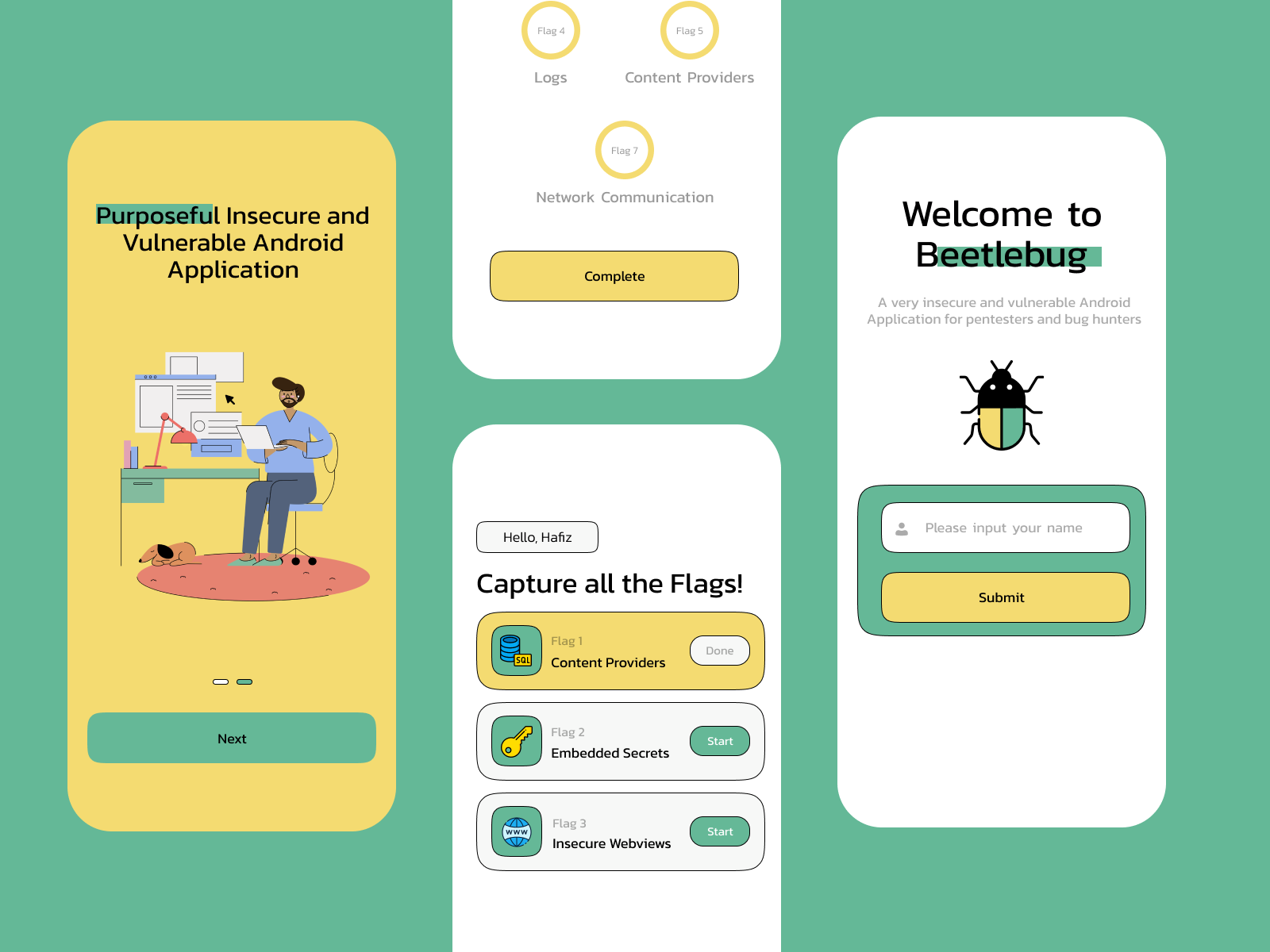
The following is a UX/UI Design Case Study describing how I designed Beetlebug. An open source insecure Android application with CTF challenges built for Android Penetration Testers, Developers, and Mobile Security enthusiasts. Through this case study, I’ll be sharing my detailed process and reasoning behind the design decisions I took to developing my very own CTF[…]
Late in the year 2020 (yes that year), Apple did something interesting. It released it’s first computer NOT running an x86 CPU. This is a big step, and Apple decided to use the ARM architecture, basically the same architecture they use in their phones, watches, and tablets. I am not going to dwell on the specifics, there[…]
Wanna know how to get started with bug bounties and why do thousands of security researchers from all over the world spend their time on public bug bounties? Then this post is for you. Bug bounties are something which is a trend nowadays. Cybersecurity jobs today are not confined to only penetration testing and vulnerability[…]